› Fora › ASTRO-FORUM › NYT FRA VIDENSKABEN › Foo over UDP eller FOU
Tagget: Security
- Dette emne har 1 svar og 1 stemme, og blev senest opdateret for 6 år, 1 måned siden af Bjarne. This post has been viewed 579 times
-
ForfatterIndlæg
-
27. januar 2018 kl. 14:42 #316083
BjarneModerator- Super Nova
Jonathan Corbet explaines UDP tunneling
Tunneling protocols are increasingly important in modern networking setups. By tying distant networks together, they enable the creation of virtual private networks, access to otherwise-firewalled ports, and more. Tunneling can happen at multiple levels in the networking stack; SSH tunnels are implemented over TCP, while protocols like GRE and IPIP work directly at the IP level. Increasingly, though, there is interest in implementing tunneling inside the UDP protocol. The “foo over UDP” (FOU) patch set from Tom Herbert, which has been pulled into the net-next tree for 3.18, implements UDP-level tunneling in a generic manner.
Why UDP? Just about any network interface out there has hardware support for UDP at this point, handling details like checksumming. UDP adds just enough information (port numbers, in particular) to make the routing of encapsulated packets easy. UDP can also be made to work with protocols like Receive Side Scaling (RSS) and the Equal-cost multipath routing protocol (ECMP) to improve performance in highly connected settings. The advantages of UDP tunneling are enough that some developers think it’s going to become nearly ubiquitous in the coming years.
Packet encapsulation and tunneling over UDP is a relatively straightforward concept to understand. Suppose a simple TCP packet is presented to the tunneling interface:
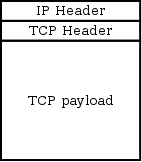 This packet has the usual IP and TCP headers, followed by the data the user wishes to send. The encapsulation process does something like this:
This packet has the usual IP and TCP headers, followed by the data the user wishes to send. The encapsulation process does something like this: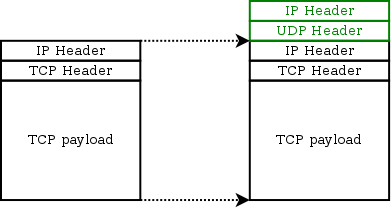 At this point, the packet looks like a UDP packet that happens to have a TCP packet buried within it. The system can now transmit it to the destination as an ordinary UDP packet; at the receiving end, the extra headers will be stripped off and the original packet will be fed into the network stack.
At this point, the packet looks like a UDP packet that happens to have a TCP packet buried within it. The system can now transmit it to the destination as an ordinary UDP packet; at the receiving end, the extra headers will be stripped off and the original packet will be fed into the network stack.Her er lidt baggrund for forståelse af TCP og UDP protokollerne:
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts communicating by an IP network. Major Internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP. Applications that do not require reliable data stream service may use the User Datagram Protocol (UDP), which provides a connectionless datagram service that emphasizes reduced latency over reliability.
En TCP pakke kan underkastes Deep Package Inspection (DPI) af en udbyder. Dette betyder, at udbyderen kan læse indholdet (hvis det ikke er krypteret med f.eks. SSH). Der er i bogstaveligste forstand tale om et åbent internet, hvor intet er skjult.
In computer networking, the User Datagram Protocol (UDP) is one of the core members of the Internet protocol suite. The protocol was designed by David P. Reed in 1980 and formally defined in RFC 768. With UDP, computer applications can send messages, in this case referred to as datagrams, to other hosts on an Internet Protocol (IP) network. Prior communications are not required in order to set up communication channels or data paths.
UDP uses a simple connectionless communication model with a minimum of protocol mechanism. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no handshaking dialogues, and thus exposes the user’s program to any unreliability of the underlying network; There is no guarantee of delivery, ordering, or duplicate protection.
UDP is suitable for purposes where error checking and correction are either not necessary or are performed in the application; UDP avoids the overhead of such processing in the protocol stack. Time-sensitive applications often use UDP because dropping packets is preferable to waiting for packets delayed due to retransmission, which may not be an option in a real-time system.
UDP har kun en længde og en checksum. Det vigtige er, at en UDP pakke ikke kan underkastes DPI. Udbyderen kan ikke få kendskab til indholdet. Figurerne ovenfor viser, hvordan man kan indkapsle en TCP pakke i en UDP pakke. TCP pakken optræder som nyttelast i UDP pakken. TCP pakken frigives, når UDP pakken er nået frem til bestemmelsesstedet, dvs en IP adresse med et bestemt portnummer. En sådan konstruktion kaldes en UDP tunnel. Der er af uransagelige grunde en tradition for i programmeringskredse at kalde en variabel størrelse for Foo. En UDP tunnel, som sender en relevant protokolpakke over denne tunnel, kaldes derfor Foo over UDP eller FOU.
Et VPN-netværk benytter sig af en FOU, så indholdet ikke kan aflyttes undervejs.
27. januar 2018 kl. 14:48 #316084
BjarneModerator- Super Nova
Jeg ved godt, at dette ikke er Rocket Science, men jeg håber, at princippet har en vis interesse i dette forum.
-
ForfatterIndlæg
- Emnet 'Foo over UDP eller FOU' er lukket for nye svar.